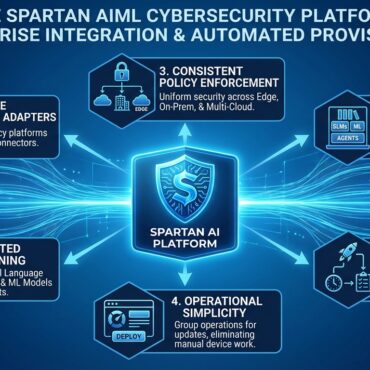
Redefining Trust at the Edge
Redefining Trust at the Edge The Spartan AI platform utilizes four primary approaches designed specifically for the unique challenges of Edge-AI environments: ✅ Ease of Integration: The platform is designed for “plug-and-play” capability, allowing it to integrate seamlessly into existing enterprise environments. ✅ Continuous On-Chip Machine Learning and Inference: Recognizing that threats [...]
















